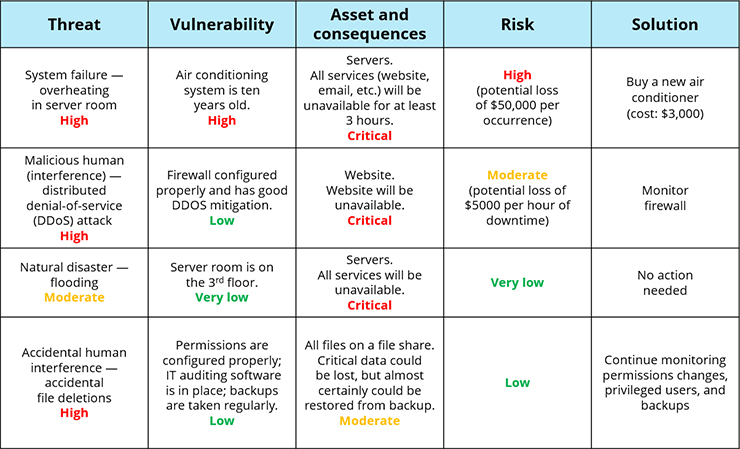
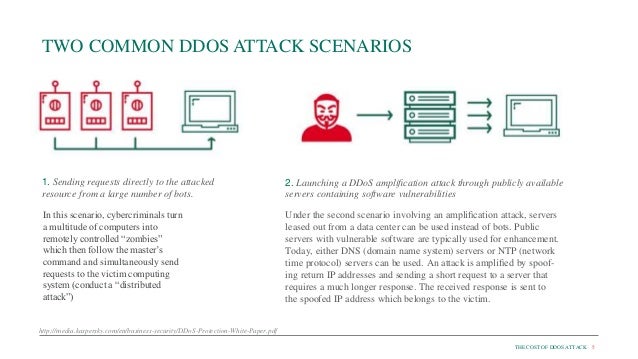
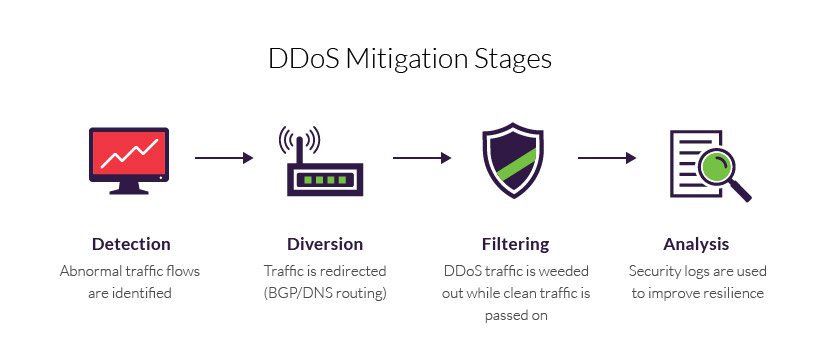
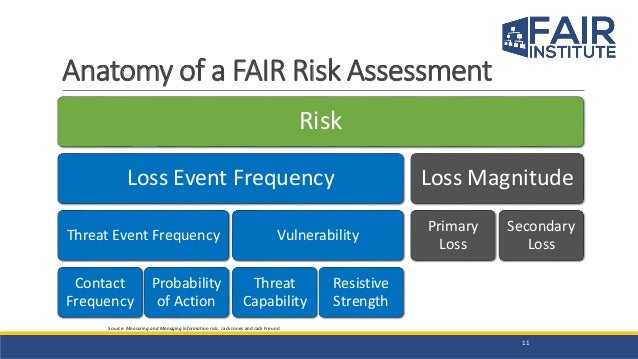
Ddos Risk Assessment Template

Phas anyone completed a ddos risk assessment recently and would be interested in sharing the templatep.
Ddos risk assessment template. Ddos risk assessment a guide to assessing your vulnerability to distributed. As distributed denial of service ddos attacks become increasingly prevalent having a strategy in place to protect your digital assets and infrastructure is key. Esec forte ddos stress testing platform provides organisations at risk of attack with a real time controlled ddos attack and also test the efficacy of ddos defense mechanism. If you are an incident handler looking to take on the management of a non ddos security incident see the related incident questionnaire cheat sheet.
Advantages of ddos stress testing. Several cyber security risk assessment and root cause analysis methods propose incident data as a source of information. Tom schauer ceo trustcc. Addressing ddos in risk assessments.
All this implies that ddos mitigation is not just about finding a pattern and putting security mechanisms in to block and filter malicious traffic. You can also edit the word version for you own needs. The inherent risk profile identifies activities services and products organized in the following categories. Ddos risk assessment true ddos attack preparedness is knowing your weaknesses not blindly implementing a vendor solution andrew shoemaker founderceo organizations frequently implement ddos attack defenses in an ad hoc manner based upon vendor recommendations or during the panic following an attack.
Technologies and connection types. This cheat sheet offers tips for battling a network distributed denial of service ddos attack on your infrastructure. Cyber security risk assessment of a ddos attack. To print use the one sheet pdf version.
Implementing an adequate ddos security template should therefore involve consideration of structural defenses in addition to the responsibilities of the it department and the staff. But it needs to be the right strategy tailored to your. However it is not a. The impact of a ddos attack is far reaching and can paralyze a business operations with significant loss in revenue and company reputation.
Inherent risk profile part one of the assessment identifies the institutions inherent risk.