Datum Security Diagram
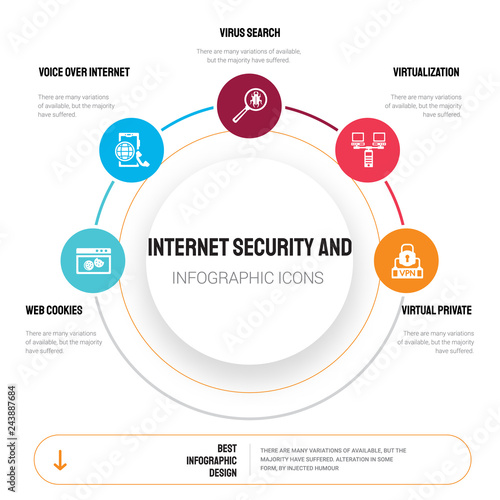
To provide a security model that satisfies numerous unique real world business cases salesforce provides a comprehensive and flexible data security model to secure data at different levels.
Datum security diagram. The network components and topology section of the ffiec operations handbook also discusses network diagrams so no one should be faulted for incorrectly assuming their network diagram counted as a data flow diagram. The task of networks protection is particularly acute for enterprises and companies that use the internet to transmit their data in this case it is important to ensure the data protection during their transmission over the communication lines to guarantee the reliable information storage. Variety of home security system wiring diagram. The network security diagrams solution presents a large collection of predesigned cybersecurity vector stencils cliparts shapes icons and connectors to help you succeed in designing professional and accurate network security diagrams network security infographics to share knowledge about effective ways of networks protection with help of.
However a dfd is a completely different requirement than a network diagram and serves a different but very useful purpose. A wiring diagram is a simplified traditional pictorial depiction of an electrical circuit. Visio diagrams that are connected to data. When cybersecurity professionals started threat modeling they borrowed the concept of data flow diagrams dfd from system engineers.
Because your diagram data is not shared or stored outside of your device and the platform where you save your diagram drawio can help you achieve certification under the iso 27000 27001 and 27002 standards the three worldwide standards that cover data protection. And if you are using drawio for confluence you can diagram your processes. Data security diagrams data is considered as an asset to the enterprise and data security simply means ensuring that enterprise data is not compromised and that access to it is suitably controlled. The following data sources are supported by visio services.
The goal of the information systemdata flow diagram is to capture the main components of an information system how data moves within the system user interaction points and the authorization boundary. The mature application and it system deconstruction comes from process flow diagrams pdf which were developed specifically for cybersecurity threat modeling. Salesforce also provides sharing tools to open up and allow secure access to data based on business needs. Lets break dfds down a little bit.
Once an administrator has configured visio services to enable connections to a particular data source there are additional security configurations that must be made depending on the kind of the data source.